A story about Schema, structured data and robots

Once upon a time, there was a little robot who came to a website to try to figure out what it was all about. The robot read some words and followed some links and thought: “Well, there are a lot of mentions of this particular word, so the page must be about that!” She sent out a message to the mother ship to file the page in a giant index so the page could be retrieved whenever somebody needed to know about that word. The robot worked very long hours for a very long time to file all the pages into the index that she could find.
After a couple of years of filing away pages, the robot became very clever indeed. Her boss at the mother ship trained her to read better and faster so she could better understand what any page was about. She could even tell when it would make most sense to show it. She even learned how to use context to judge a piece of writing instead of just finding mentions of a particular term.
But, smart as the robot had become, her creators needed extra help to get her to fully understand the world. The robot did not have the capacity to grasp every single piece of knowledge and understand how all these pages were connected.
Luckily, some clever humans created something incredibly clever called Schema, which was a bit like a giant thesaurus for robots just like our little hero.
In it, she found everything she needed. It told her what she could look for to determine what a particular page was about, be it a product, an event or even a person. She learned about different movies, books and authors. About recipe ingredients and cooking instructions. She found out how people relate to each other, to past events and to abstract concepts that were always a mystery to her. Everything she read was instantly clear to her — she was so incredibly happy!
Websites which used this Schema thesaurus helped her, and all the other robots like her, to make sense of the world. She finally knew everything. In return, she rewarded those sites with spectacularly colourful listings when people looked for them. But she could only reward those sites who implemented it well and that became a problem for other sites who didn’t know how to use it properly.
She soon found that there was a lot lacking regarding Schema. Many sites offered only tiny pieces of the magical Schema data and none of it was connected to the sources that could help her do her job better. She tried asking for help – pleading with site owners to improve the way they used SCHEMA, but to no avail. Until, many years later, a hugely popular plugin for the biggest content management system in the solar system stepped in to help out the little robot.
Tentatively, she looked at the internals of the Schema implementation of the plugin, codename Yoast SEO 11.0. “Wow, this is just what I need!”, she said. “I’ve never seen anything like this before! This is Schema that I can read and understand. It is complete, it shows me where pages are and how people and organizations connect. Most importantly, it is interconnected! I no longer have to guess where everything goes. It’s all in a graph – a neat little package – ready for me to read, understand and file away!”
And they all lived happily ever after.
(Yes, your author has read Marieke’s posts on storytelling)
Results of using Schema structured data
Schema-powered structured data is one of the hardest, most abstract pieces of web technologies to describe, while also being one of the most important ones. I hope the story above has made the concept a lot clearer for you. Now that you’ve formed a mental image of what we’re talking about here, let me show you what adding structured data to your site can lead to.
Before you read on: we’ve recently launched the Understanding structured data training course. This course helps you understand structured data in detail and teaches you how to improve your own chances of getting rich results. Get access to this course, all of our other SEO courses and extra features in Yoast SEO by going Premium:
A better understanding of your site
We always say you should do everything in your power to help both search engines and searchers to find out what your site is about. Using structured data gives you superpowers in the eyes of the search engine. Since you are labeling the most important parts of your content or site elements and connecting them to other parts, you are making sure that search engines truly understand your site. No longer do they have to guess about what everything means — you can just tell them.
Getting stuff into Google’s Knowledge graph gets a lot easier once you add relevant Schema to your site. Not only that, other platforms like Pinterest love this kind of data as well.
With Yoast SEO 11.0, we’re not only making it easier for search engine robots to read your site, but also to understand. We do this by making connections and offering the structured data in a so-called graph. See the image below for a graphical representation of this idea:
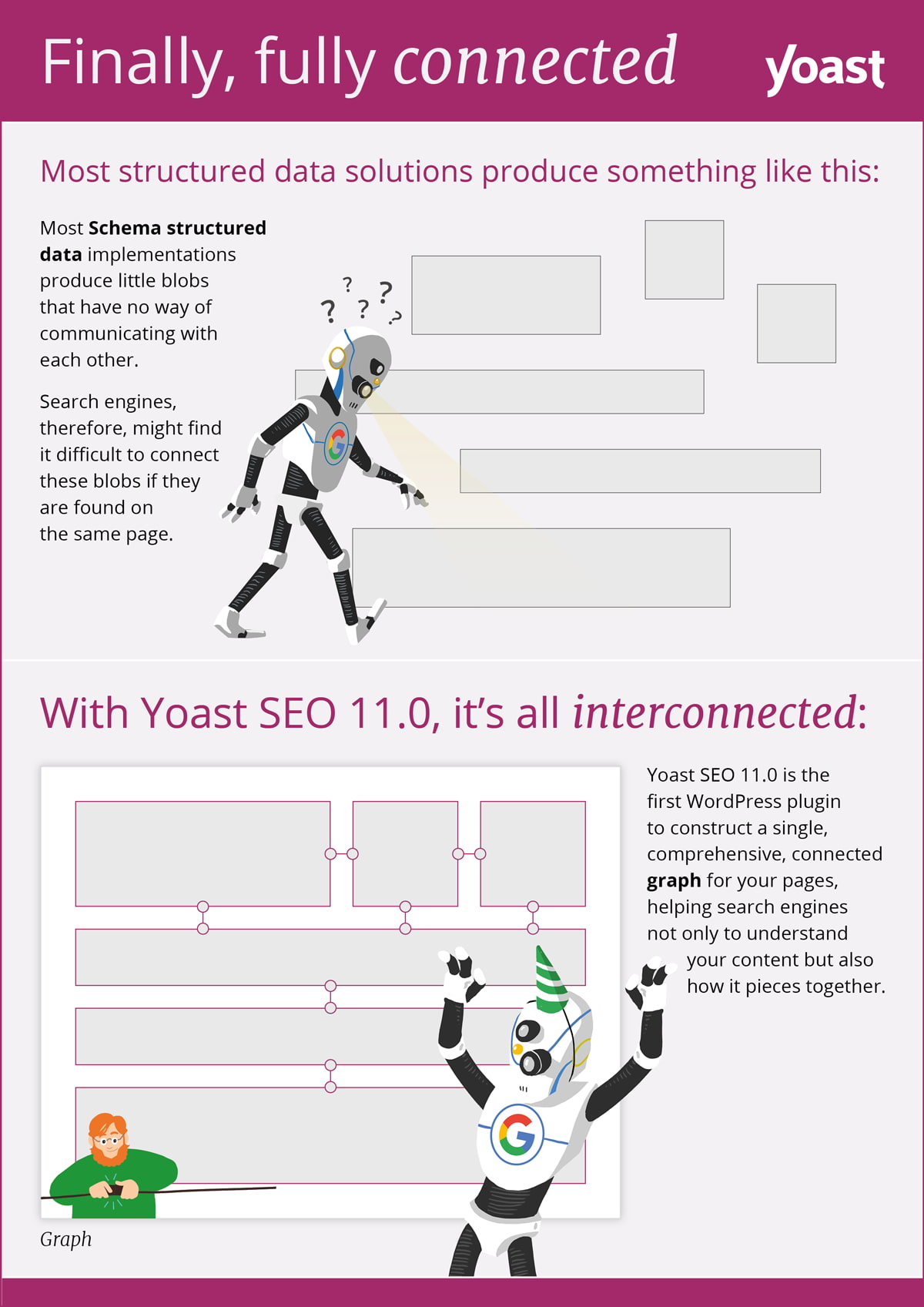
Rich results
Another reason for implementing structured data is the spectacular shiny stuff our robot heroine promised: rich results. Rich results are enhanced search results and they come in many forms, from star ratings to fully enhanced recipe snippets. Many are powered by structured data, but sometimes, you get them without doing anything — besides having an awesome site, of course.
Here is an example of a structured data powered rich result:
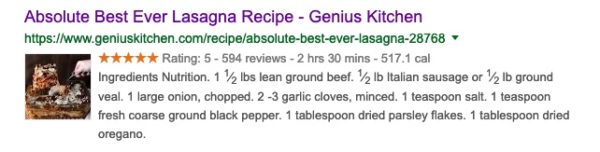
With the new structured data implementation in Yoast SEO 11.0, you get a firm foundation to build on. While you’ll have a bigger chance of getting rich results by using Yoast SEO, there’s no guarantee that you’ll get them — in the end, the search engines decide who gets what.
Here’s a selection of what we do at the moment. You can find a complete overview of all Google’s current rich results in the Search Gallery:
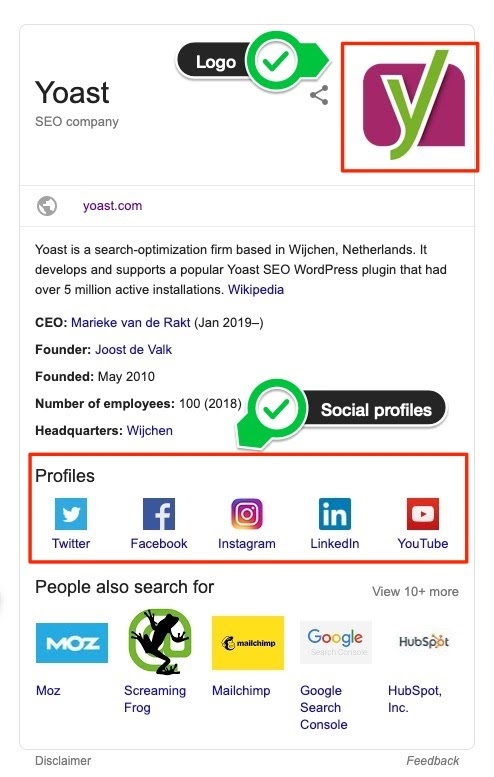
Logo and social profiles in the Knowledge graph
If you have an Organization, you can get its logo to show up in the Knowledge panel. The same goes for social profiles. Simply add these in the settings of Yoast SEO and they’ll eventually show up.
Personal graphs
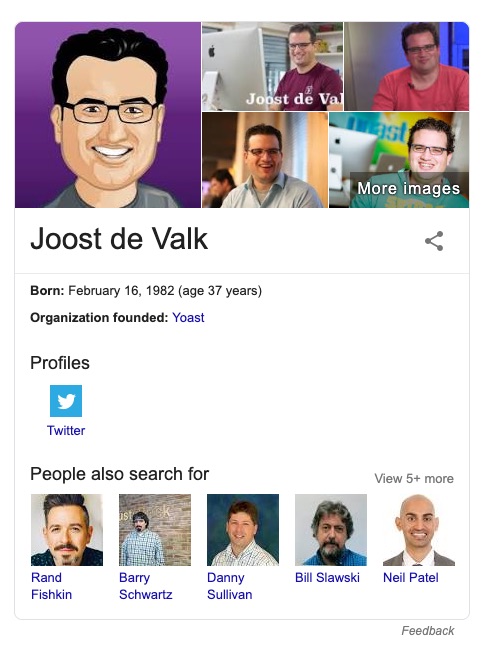
If you have a site representing a person, you can add the necessary social accounts. Your image will be grabbed from Gravatar. You can set this in Yoast SEO. Not every person will get a Knowledge graph panel — there’s more at play here. Google combines this input with other sources to build a panel. Once you have one, you can claim it and suggest edits.
Articles
Search engines might do cool stuff with articles marked up with structured data. For news publishers, this is important because this might also mean a top spot in the news carousel. For this, you need NewsArticle Schema in your articles and our News SEO plugin provides this for you. Yoast SEO itself, automatically adds regular Article structured data to your articles, including information about the author and how the page connects to the main entity of the site.
Local business
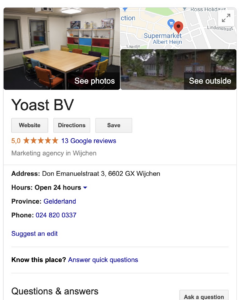
Our Local SEO plugin takes care of everything you need to get your local business correctly visible in the search engines. You can add opening hours, geographical information, contact information, business locations — including multiple locations under one name, et cetera.
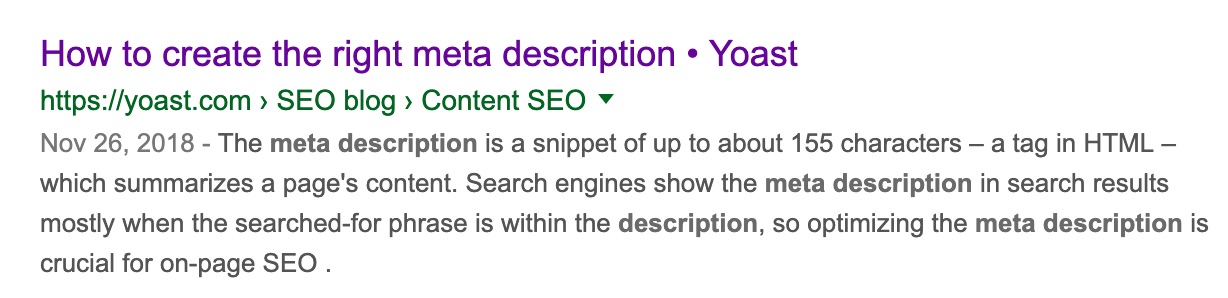
Breadcrumbs
A breadcrumb is a navigational tool that helps searchers and search engines figure out where they are on your site. If you activate this in Yoast SEO, you might get something like this in the search results:
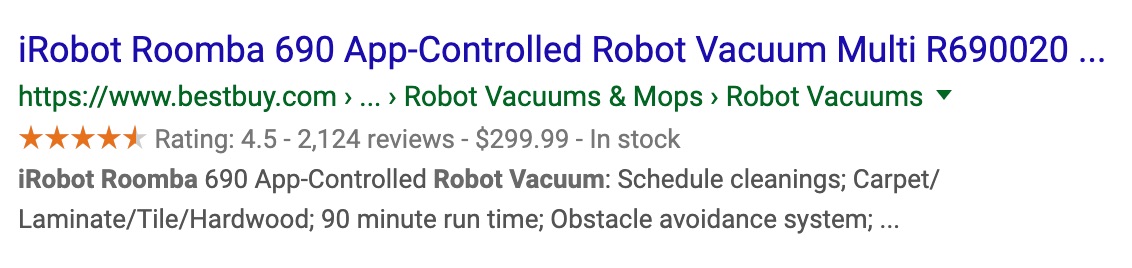
Products
Our WooCommerce plugin adds a cool possibility for getting rich results for products. If you combine this with other structured data, you can get really expansive rich results in search results with ratings and everything. You can also be featured in image search and different product carousels. In addition, Pinterest will pick up the main product on your page more easily.
Structured data is hot
This article, including the adventures of our little robot, aims to show you a small sampling of structured data powered search results. Working with structured data was always hard, but we’re fixing that — and you don’t have to do much for it! If you want to learn more about structured data, we have a free Structured data for beginners course and an Understanding structured data course that goes into more detail.
Yoast SEO 11.0 has a completely rebuilt structured data framework that adds more sensible, and more importantly, interconnected structured data to your site. Search engines can pick this up and do interesting things with. We’re not done yet, because we have a lot more cool stuff coming up!
Read more: Schema structured data is hard, but we’re making it easy

We have product pages setup as regular, non-WooCommerce pages. Can Yoast tag them as product schema?
On the new update of Yoast today, Knowledge Graph & Schema.org section, I get the option of Person and organization but not a company. Our blog is about beauty, lifestyle, and shopping. I didn’t know what to choose. the company seems best for us.
Hey Suanlian,
A company is a type of organization; that’s probably the best choice for your site! :)
Thank you! Will switch to organization.