Why have control of where search engines go?
It may sound surprising, but not all pages on your website help you rank. Certainly, the pages that help your visitors and answer their questions are your SEO superstars. But some content does not belong on the search results pages, like your admin, login and thank you pages. So what can you do?
How Yoast SEO can help you with this
- Gain site wide control of the appearance of your content
- Decide what happens to individual posts and pages
- Guide visitors to the right pages on your site
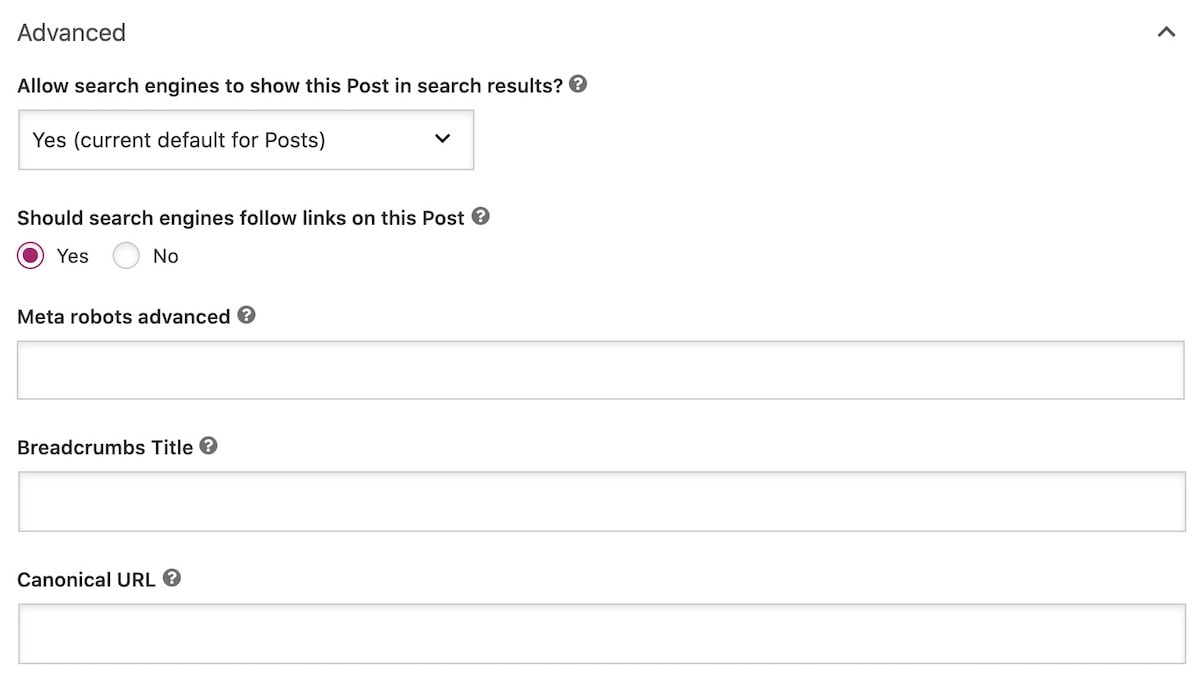
How to add robots meta tags with Yoast SEO
Yoast SEO lets you talk to search engines. With the flip of a switch, you can tell them which URLs they should exclude from the search results (noindex). And, you can also prevent search engines from valuing links on a page (nofollow).
Get your Yoast SEO Premium subscription
Yoast SEO Premium also comes with a multiple keyword functionality and premium support so be sure to check out all features of Yoast SEO Premium.
Why do I need to tell search engines what to do?
You want to make your audience and search engines happy, right? You can do that by critically evaluating your pages, and excluding those with no value from the search results. In Yoast SEO you get the power to decide what search index, which directly influences your audience’s experience!
Gain site wide control of the search appearance of your content
Choose which taxonomies to include or exclude
Category and tag archives can serve as landing pages and help your rankings. In fact, adding rich content to these types of pages can make them some of your best pages! But sometimes, you might want to noindex these pages. Yoast SEO lets you do that with the flick of a switch.
Keep date archives out of search engines
If your website uses dates in the URLs, you probably have lots of low-value pages. Each date, month, and year archive page contains largely duplicate content and provides little value to the user as a landing page. They can be helpful for navigation and discovery, but, usually shouldn’t be indexed by search engines. With Yoast SEO you can keep these pages for user navigation, but prevent Google from indexing them.
Fix single author websites
If your website only has one author or user, then chances are, your author archive pages are just a copy of your home page. Search engines might view that as duplicate content, and that can hurt your rankings. Yoast SEO lets you noindex your author archives, so they are out of sight for search engines and users!
Noindex other content types
In Yoast SEO you can set noindex as a default for posts, pages, or other types of content. For example, if you use WooCommerce or some of our other plugins, you might have additional content types like product or location pages.
Decide what happens to individual posts and pages
What do a login page and a ‘thank you’ page have in common? They both have no SEO value. The best course of action is to remove such pages from search engines.
What about posts? You might want to noindex old posts which need some extra work. A noindex tag can come in handy until you update the post and make it ready to stand proudly on the search results page.
Let Yoast SEO control the technical stuff in the background
Yoast SEO works hard behind the scenes to facilitate the dialogue between your site and search engines. In our developer documentation, you can learn more about how we manage and generate meta robot tags.
How do noindex and nofollow work in Yoast SEO?
When you are certain that you want to add noindex or nofollow directives to a page, Yoast SEO lets you do it in a few clicks.
Site-wide controls
In the search appearance settings of Yoast SEO (located in the ‘Content type’ section), you can access the site-wide settings that allow you to control the indexing defaults for each of your content types. It’s a matter of switching a toggle on or off!

Individual posts and pages
To nofollow or noindex individual posts or pages, head to the Advanced tab of the Yoast SEO Meta box. Again, here, all you need to do is select a few radio buttons, and you are good to go!
So, if you want to have control of where search engines go on your site and what they’re allowed to index, the Yoast SEO plugin helps you out! Of course, that’s not all our plugin does. Make sure to take a look at the other features it has to offer.

Also available in Yoast SEO for Shopify
This feature is also available in Yoast SEO for Shopify. Read more on this feature and how it is adapted for use in online stores.
Get your Yoast SEO Premium subscription
Yoast SEO Premium also comes with a multiple keyword functionality and premium support so be sure to check out all features of Yoast SEO Premium.
Let Yoast SEO help you win the search rankings
Discover all the features of the Yoast SEO for WordPress plugin.